In an era where digital transformation is reshaping industries, enterprise resource planning (ERP) systems have become the backbone of business operations. These systems integrate critical processes like finance, supply chain, and customer management, making them indispensable for organizational success.
However, this centralization of sensitive data also makes ERP systems a prime target for cyberattacks. Alarmingly, nearly 90% of cybersecurity experts anticipate an increase in attacks against ERP systems within the next year, underscoring the urgent need for enhanced ERP security.
The consequences of an ERP breach can be catastrophic, ranging from financial loss and operational disruptions to reputational damage and regulatory penalties. As businesses increasingly rely on cloud-based ERP solutions, the risks associated with misconfigurations, unauthorized access, and insider threats continue to grow. To safeguard these mission-critical systems, organizations must implement robust security measures and foster a culture of cybersecurity awareness.
Deskera ERP stands out as a secure and scalable solution, trusted by businesses of all sizes. With built-in features such as multi-factor authentication, regular security updates, and advanced role-based access controls, Deskera helps mitigate vulnerabilities effectively.
Additionally, its AI-powered assistant, David, ensures proactive monitoring, reducing the likelihood of breaches. By choosing Deskera, companies can confidently manage their operations while prioritizing data security.
This blog explores the evolving landscape of ERP security, common challenges, and actionable best practices to protect your business data. Whether you're evaluating a new ERP system or looking to strengthen the security of your existing one, this guide offers valuable insights to help you stay ahead of potential threats.
What Is ERP Security?
ERP security refers to the strategies, practices, and technologies implemented to safeguard enterprise resource planning (ERP) systems from unauthorized access, data breaches, cyberattacks, and other threats.
ERP systems are integrated platforms that manage critical business processes, such as finance, supply chain, human resources, and customer relationship management, making them a central repository for sensitive organizational data.
Given the extensive amount of sensitive information stored in ERP systems, they are a high-value target for cybercriminals. ERP security involves protecting the system's infrastructure, application layers, and the data it houses. This includes access control, encryption, vulnerability management, and user training to ensure the system is resilient against internal and external threats.
Modern ERP systems, particularly those hosted in the cloud, require additional security measures, such as multi-factor authentication (MFA), secure APIs, and compliance with data protection regulations like GDPR and CCPA. Effective ERP security is essential not only for protecting sensitive data but also for ensuring business continuity and maintaining trust among stakeholders.
By adopting best practices and leveraging secure ERP solutions, organizations can mitigate risks and focus on optimizing their operations without fear of data breaches or operational disruptions.
The ERP Security Landscape: Challenges and Risks
ERP systems are the backbone of modern businesses, integrating critical operations and storing vast amounts of sensitive data. However, this centralization also makes them highly attractive targets for cyber threats. Below are the key challenges and risks organizations must address to safeguard their ERP systems effectively.
1. Growing Attack Surface
- ERP systems integrate various business functions, making them a central repository for sensitive data.
- Cloud-based ERP solutions and interconnected systems expand the attack surface for cybercriminals.
2. Misconfigurations
- Improperly implemented or default security settings leave systems vulnerable to exploitation.
- Failure to configure access controls and user permissions properly increases risk.
3. Outdated Software and Patch Management Issues
- Many organizations delay software updates, fearing operational disruptions.
- Unpatched vulnerabilities in outdated software create opportunities for cyberattacks.
4. Insider Threats
- Employees, contractors, or partners with excessive permissions may intentionally or accidentally compromise the system.
- Weak access controls enable unauthorized individuals to access critical functions or data.
5. External Cyber Threats
- Phishing Attacks: Trick employees into revealing credentials, granting attackers access to the system.
- Ransomware: Encrypts ERP data, demanding payment to restore access.
- Brute-Force Attacks: Exploit weak passwords to gain unauthorized access.
6. Compliance Risks
- Highly regulated industries face fines and reputational damage for non-compliance with data protection standards.
- A security breach may lead to violations of GDPR, CCPA, or other regulations.
By understanding these risks and implementing proactive security measures, organizations can better protect their ERP systems, maintain data integrity, and ensure business continuity.
Importance of ERP Security
ERP security is a critical aspect of modern business operations, as it ensures the protection of sensitive data, operational continuity, and regulatory compliance.
ERP systems serve as the backbone of organizations, integrating various functions such as finance, supply chain, human resources, and customer relationship management. With the increasing reliance on these systems, their security becomes indispensable for sustaining business success in the digital age.
Key reasons why ERP security is crucial are:
Protection of Sensitive Data
- ERP systems house a wealth of sensitive information, including financial records, employee details, proprietary data, and customer information.
- A breach of this data can lead to identity theft, financial fraud, and the loss of valuable intellectual property.
- Robust ERP security mechanisms, such as encryption, role-based access control, and multi-factor authentication, are essential to prevent unauthorized access and data leaks.
Ensuring Business Continuity
- Cyberattacks targeting ERP systems can disrupt operations, causing downtime that impacts productivity and revenue.
- For instance, ransomware attacks can lock businesses out of their critical systems, halting operations until a ransom is paid or data is recovered.
- Implementing comprehensive ERP security safeguards ensures that systems remain operational and data remains accessible during a cyber threat or disaster.
Compliance with Regulatory Requirements
- Laws and regulations like GDPR, CCPA, HIPAA, and industry-specific standards impose strict guidelines on data security and privacy.
- Non-compliance can result in heavy fines, legal challenges, and reputational damage.
- ERP security measures, including audit trails and secure data handling practices, help businesses meet regulatory requirements while ensuring the ethical use of data.
Preservation of Reputation and Customer Trust
- A security breach can erode customer trust, tarnish a brand's reputation, and lead to the loss of loyal customers.
- Negative publicity following a breach can deter potential clients and partners, impacting long-term business growth.
- Proactively safeguarding ERP systems with strong security measures demonstrates a commitment to protecting stakeholders' interests, reinforcing trust in the organization.
Preventing Financial Loss
- The financial repercussions of ERP security breaches can be significant, encompassing both direct and indirect costs.
- Direct costs include ransom payments, recovery expenses, and fines, while indirect costs may involve lost revenue, legal fees, and increased insurance premiums.
- Strong ERP security measures, such as regular updates, penetration testing, and advanced monitoring systems, help prevent these financial losses.
Investing in ERP security goes beyond protecting digital assets—it’s about securing the future of the organization. A comprehensive approach to ERP security ensures that businesses can operate with confidence, maintain stakeholder trust, and navigate the complexities of the digital landscape without disruption.
12 ERP Security Best Practices: Building a Resilient Framework
Securing ERP systems is essential to protecting sensitive data, ensuring operational continuity, and meeting regulatory requirements.
Given the critical role ERP systems play in integrating and managing business processes, a comprehensive security framework is indispensable.
Below are 12 detailed best practices to help organizations build a resilient ERP security strategy.
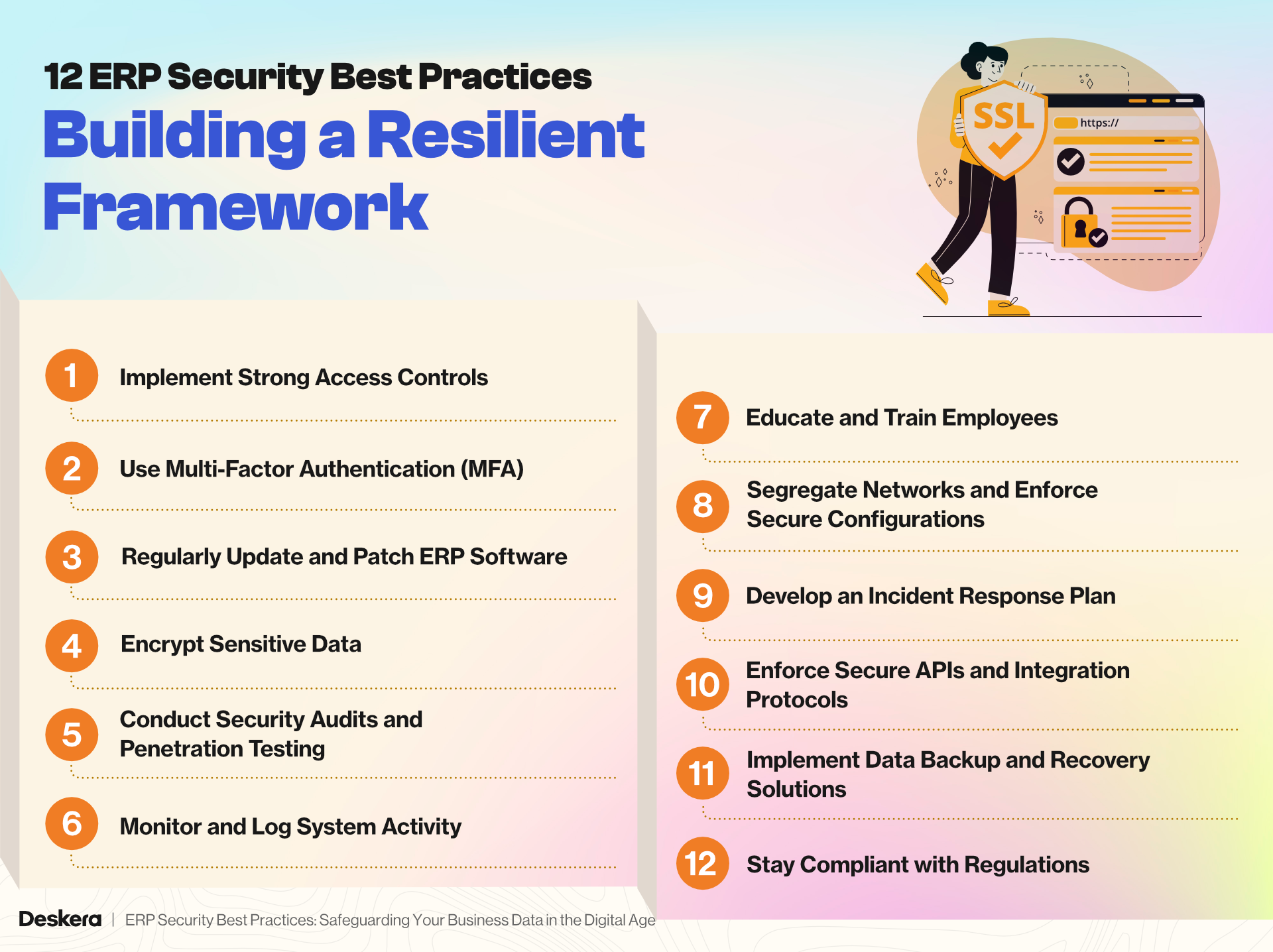
1. Implement Strong Access Controls
- Define user roles and permissions using Role-Based Access Control (RBAC) to restrict access based on job responsibilities.
- Enforce the principle of least privilege, allowing users only the access necessary to perform their tasks.
- Regularly review and update access permissions to remove unnecessary or outdated roles, especially for departing employees or contractors.
2. Use Multi-Factor Authentication (MFA)
- Strengthen authentication by requiring users to verify their identity through two or more factors, such as passwords, biometrics, or one-time passcodes.
- Apply MFA universally across the ERP system, including for administrative and privileged accounts.
- Monitor for suspicious login attempts and flag repeated failed attempts for immediate action.
3. Regularly Update and Patch ERP Software
- Keep ERP software up to date by applying vendor-released patches and updates promptly.
- Automate patch management wherever possible to streamline the process and reduce human error.
- Test patches in a sandbox environment before deployment to ensure compatibility and minimize disruptions.
4. Encrypt Sensitive Data
- Encrypt data at rest using robust algorithms like AES-256 to safeguard stored information.
- Secure data in transit using protocols such as HTTPS and SSL/TLS to protect information exchanged between systems.
- Implement encryption key management policies to prevent unauthorized access to encryption keys.
5. Conduct Security Audits and Penetration Testing
- Schedule regular security audits to assess the ERP system for vulnerabilities, misconfigurations, and compliance issues.
- Hire certified penetration testers to simulate attacks and uncover potential security gaps.
- Use findings from audits and tests to strengthen your ERP security measures and address vulnerabilities promptly.
6. Monitor and Log System Activity
- Deploy Security Information and Event Management (SIEM) tools to continuously monitor ERP system activities.
- Establish logs for key activities, including logins, data access, and configuration changes, to track user actions.
- Analyze logs regularly to identify patterns or anomalies that could indicate security threats.
7. Educate and Train Employees
- Conduct regular training sessions to educate employees about common security threats, such as phishing and social engineering.
- Emphasize the importance of creating strong, unique passwords and using secure methods for sharing sensitive information.
- Provide role-specific training to employees who interact directly with the ERP system.
8. Segregate Networks and Enforce Secure Configurations
- Segment ERP systems from public networks and other internal systems to reduce the impact of potential breaches.
- Use firewalls and intrusion detection/prevention systems to monitor and control traffic between network segments.
- Review and harden ERP system configurations, disabling unused features and services that may pose security risks.
9. Develop an Incident Response Plan
- Create a comprehensive incident response plan outlining roles, responsibilities, and procedures in the event of a security breach.
- Include steps for isolating affected systems, notifying stakeholders, and recovering operations.
- Conduct regular drills and tabletop exercises to test and refine the incident response plan.
10. Enforce Secure APIs and Integration Protocols
- Ensure that APIs connecting the ERP system to external applications or tools are secure and up to date.
- Use API gateways to authenticate and monitor API traffic, preventing unauthorized access.
- Encrypt data transmitted through APIs and adopt protocols like OAuth 2.0 for secure authentication.
11. Implement Data Backup and Recovery Solutions
- Schedule automatic, regular backups of ERP data to ensure data availability in case of cyberattacks or system failures.
- Store backups securely, both on-site and off-site, and use encryption to protect backed-up data.
- Test data recovery procedures periodically to verify that backups can be restored quickly and completely.
12. Stay Compliant with Regulations
- Align ERP security policies and practices with relevant regulatory frameworks, such as GDPR, CCPA, HIPAA, or industry-specific standards.
- Conduct regular compliance audits to identify gaps and address them proactively.
- Stay updated on changes in data protection laws and adjust ERP security measures accordingly.
By implementing these detailed best practices, organizations can fortify their ERP systems, mitigate risks, and build trust with stakeholders. A robust security framework not only safeguards sensitive data but also ensures the smooth operation of critical business processes.
User Awareness: The Human Element in ERP Security
While technology plays a critical role in securing ERP systems, the human element remains one of the most significant factors in determining the effectiveness of security measures. Employees, vendors, and even third-party contractors often have access to ERP systems, making user awareness and behavior a cornerstone of a robust security strategy.
Here's why user awareness is vital and how organizations can foster a security-first culture:
The Role of Users in ERP Security
- First Line of Defense: Employees often serve as the first line of defense against cyber threats like phishing or social engineering. Their ability to recognize and respond appropriately to threats is crucial.
- Potential Weak Points: Human error, such as clicking on malicious links or using weak passwords, accounts for a large proportion of data breaches. Users who are unaware of security protocols can unintentionally expose ERP systems to vulnerabilities.
Challenges of Managing the Human Element
- Lack of Training: Many employees are unfamiliar with security best practices, especially those not directly involved in IT or cybersecurity roles.
- Overconfidence: Some users may underestimate the complexity of cyber threats, assuming that existing security measures will protect them regardless of their actions.
- Access Mismanagement: Users with excessive or inappropriate access privileges can inadvertently misuse their permissions, leading to data leaks or system misconfigurations.
Strategies to Improve User Awareness
- Comprehensive Training Programs
- Provide regular training tailored to the roles and responsibilities of employees.
- Cover topics such as recognizing phishing attempts, secure password practices, and handling sensitive data within the ERP system.
- Simulated Cybersecurity Drills
- Conduct mock phishing campaigns and other simulated attacks to test employee readiness.
- Offer constructive feedback to improve response rates and behavior during real threats.
- Clear Communication of Security Policies
- Create easy-to-understand guidelines for ERP security protocols.
- Ensure that employees know whom to contact in case of suspicious activity or security concerns.
- Gamification and Rewards
- Use gamified elements to encourage security awareness, such as quizzes or leaderboards for completing training modules.
- Reward employees who demonstrate exemplary adherence to security practices.
Fostering a Security-First Culture
- Leadership Involvement: Management should actively participate in and endorse security initiatives, emphasizing their importance at all organizational levels.
- Regular Updates: Continuously update employees on emerging threats and evolving ERP security protocols.
- Empower Users: Encourage employees to take ownership of their role in protecting ERP systems, fostering a sense of responsibility and vigilance.
The Impact of User Awareness
When users are well-informed and proactive, they become a key asset in the fight against ERP security threats. A culture of awareness reduces the likelihood of successful attacks and bolsters the effectiveness of technological measures.
By prioritizing the human element, organizations can build a more comprehensive and resilient ERP security framework.
Advanced Security Technologies for ERP Systems
As cyber threats become increasingly sophisticated, traditional security measures are no longer sufficient to protect ERP systems effectively. Organizations must adopt advanced technologies to safeguard their critical business operations and sensitive data.
These cutting-edge tools not only enhance security but also provide proactive mechanisms to detect and respond to potential vulnerabilities. Below are some of the most impactful advanced security technologies for ERP systems.
1. Artificial Intelligence and Machine Learning
- Behavioral Analytics: AI-powered systems analyze user behavior patterns to detect anomalies, such as unusual login times or abnormal data access.
- Threat Prediction: Machine learning algorithms identify emerging threats by analyzing vast datasets, enabling organizations to act before breaches occur.
- Automation: AI automates routine security tasks, such as log analysis and incident response, improving efficiency and accuracy.
2. Blockchain Technology
- Immutable Records: Blockchain secures ERP transactions by creating immutable and tamper-proof records, ensuring data integrity.
- Decentralized Security: The distributed ledger minimizes single points of failure, reducing the risk of unauthorized access or data breaches.
- Smart Contracts: Blockchain-based smart contracts enforce security policies automatically, enhancing compliance and reducing manual intervention.
3. Zero Trust Architecture (ZTA)
- Continuous Verification: ZTA requires constant authentication and authorization for every user and device attempting to access ERP resources.
- Micro-Segmentation: Dividing the ERP system into smaller, secure zones limits the potential damage of a breach.
- Context-Aware Policies: ZTA adapts security measures based on factors like user location, device health, and access requests.
4. Advanced Encryption Technologies
- Post-Quantum Cryptography: Preparing ERP systems for future threats posed by quantum computing, ensuring long-term data security.
- Dynamic Encryption: Real-time encryption and decryption of data based on access requests, minimizing exposure.
- Homomorphic Encryption: Allows computations on encrypted data without decrypting it, ensuring data privacy during processing.
5. Security Information and Event Management (SIEM) Systems
- Real-Time Monitoring: SIEM solutions aggregate and analyze data from multiple sources to provide real-time threat detection.
- Incident Response: Advanced SIEM tools automate responses to detected threats, reducing response times.
- Integration with ERP: Seamlessly integrates with ERP systems, providing comprehensive visibility into security events.
6. Identity and Access Management (IAM) Solutions
- Biometric Authentication: Advanced IAM tools incorporate facial recognition, fingerprint scanning, and voice verification for secure access.
- Adaptive Authentication: Adjusts security measures based on risk levels, such as requiring additional verification for high-risk actions.
- Privileged Access Management (PAM): Enhances the security of administrative accounts by monitoring and controlling their access.
7. Internet of Things (IoT) Security for ERP
- Device Authentication: Ensures only authorized IoT devices can connect to the ERP system.
- Data Encryption for IoT: Protects data generated and transmitted by IoT devices integrated with ERP systems.
- Threat Detection for IoT Networks: Specialized tools monitor IoT device behavior for signs of compromise.
8. Cloud Security Tools
- Cloud Access Security Brokers (CASBs): Protect data and applications hosted in cloud-based ERP systems by monitoring and enforcing security policies.
- Data Loss Prevention (DLP): Prevents unauthorized sharing or downloading of sensitive information stored in the cloud.
- Encryption and Key Management: Ensures all cloud-stored data remains encrypted and accessible only to authorized users.
9. Next-Generation Firewalls (NGFWs)
- Deep Packet Inspection: NGFWs analyze data packets entering and leaving the ERP system, identifying and blocking malicious traffic.
- Application-Aware Filtering: Provides granular control over applications interacting with ERP systems, enhancing security.
- Threat Intelligence Integration: Uses real-time data to adapt and respond to evolving threats.
10. Deception Technologies
- Honeypots and Decoys: Deploy fake ERP assets to lure attackers and study their methods without risking real systems.
- Proactive Threat Intelligence: Gather insights from attacker behavior to fortify the ERP system against similar threats.
- Attack Mitigation: Deception technologies slow down attackers, providing security teams more time to respond.
The adoption of advanced security technologies is no longer optional for businesses that rely on ERP systems. These tools offer proactive, intelligent, and adaptive security measures to address modern challenges.
By integrating such technologies, organizations can ensure their ERP systems remain secure against current and emerging threats while maintaining business continuity.
Evaluating ERP Vendors for Security Excellence
When choosing an ERP solution, evaluating the security measures provided by the vendor is crucial. Not all ERP systems are built with the same level of security, and selecting a vendor with a robust security framework can be the difference between seamless business operations and potential security disasters.
Below are key criteria and strategies for assessing ERP vendors with a focus on security excellence.
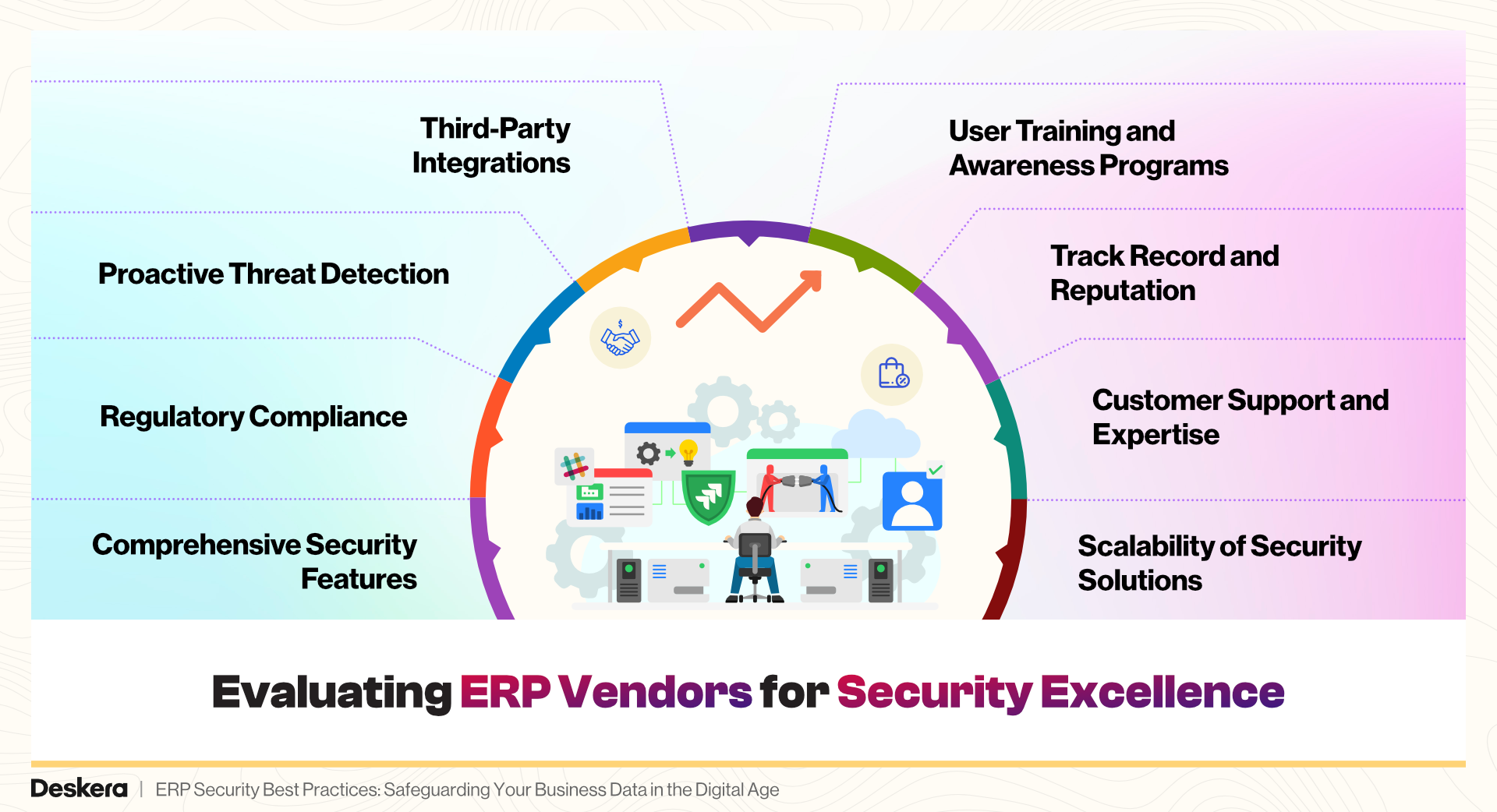
1. Comprehensive Security Features
- Data Encryption Standards: Assess whether the vendor provides end-to-end data encryption for both data at rest and in transit.
- Multi-Factor Authentication (MFA): Ensure that the vendor supports MFA to enhance login security.
- Role-Based Access Control (RBAC): Verify that the ERP system offers detailed access control mechanisms, allowing tailored permissions based on user roles.
2. Regulatory Compliance
- Certifications and Standards: Check if the ERP vendor complies with industry standards such as ISO/IEC 27001, GDPR, and other data protection regulations relevant to your business.
- Audit Trails: The system should provide comprehensive logs and audit trails to monitor user activities and maintain compliance.
- Data Residency Options: For businesses subject to local data laws, the vendor should offer data storage within specific jurisdictions.
3. Proactive Threat Detection
- Built-In Security Monitoring: Vendors that offer real-time security monitoring and threat detection tools add an additional layer of protection.
- AI and Machine Learning Capabilities: Advanced ERP systems should use AI to identify and respond to suspicious activities.
- Incident Response Plans: Evaluate the vendor’s capability to handle data breaches, including their response time and communication process.
4. Third-Party Integrations
- Compatibility with Security Tools: Ensure that the ERP system can integrate with existing security solutions, such as SIEM systems and IAM platforms.
- API Security: Investigate how secure the vendor's APIs are for seamless and safe third-party integrations.
- Vulnerability Management: Ask how the vendor handles software patches and updates for connected third-party applications.
5. User Training and Awareness Programs
- Vendor-Supported Training: Vendors that provide user training and resources on security best practices demonstrate a commitment to comprehensive security.
- Documentation and Resources: Check for well-documented guides and resources that can help your team maintain a secure environment.
- Simulated Security Drills: Some vendors offer simulations or tools to help organizations practice responding to potential security threats.
6. Track Record and Reputation
- Past Incidents: Research any past security breaches or vulnerabilities associated with the ERP vendor.
- Customer References: Speak to current or past clients about their experiences with the vendor's security protocols.
- Independent Reviews: Utilize trusted review platforms and security forums to gather unbiased feedback on the vendor’s reliability and security measures.
7. Customer Support and Expertise
- 24/7 Security Support: Ensure that the vendor offers round-the-clock customer support, particularly for security issues.
- Dedicated Security Experts: Check if the vendor provides access to cybersecurity professionals who can assist in implementing best practices.
- Incident Response Assistance: Evaluate the vendor’s ability to support your team during security incidents, from initial detection to remediation.
8. Scalability of Security Solutions
- Growing Business Needs: As your organization expands, the ERP system should be capable of scaling its security measures accordingly.
- Flexible Licensing: Vendors that offer scalable licensing options ensure that security features can be upgraded as needed.
- Custom Security Modules: Look for vendors that provide customizable security features to align with unique business requirements.
Selecting an ERP vendor goes beyond comparing basic functionality; assessing their approach to security is essential.
By focusing on these critical areas, organizations can partner with a vendor that not only meets operational needs but also fortifies the ERP system against potential threats.
This proactive evaluation helps ensure that business processes remain protected and resilient in the face of evolving cybersecurity challenges.
The Future of ERP Security: Trends and Predictions
As businesses increasingly rely on ERP systems to streamline operations and manage critical data, the future of ERP security is set to evolve rapidly.
With cyber threats becoming more sophisticated and compliance regulations tightening, organizations must stay ahead by embracing emerging trends and technologies.
Here’s what the future holds for ERP security:
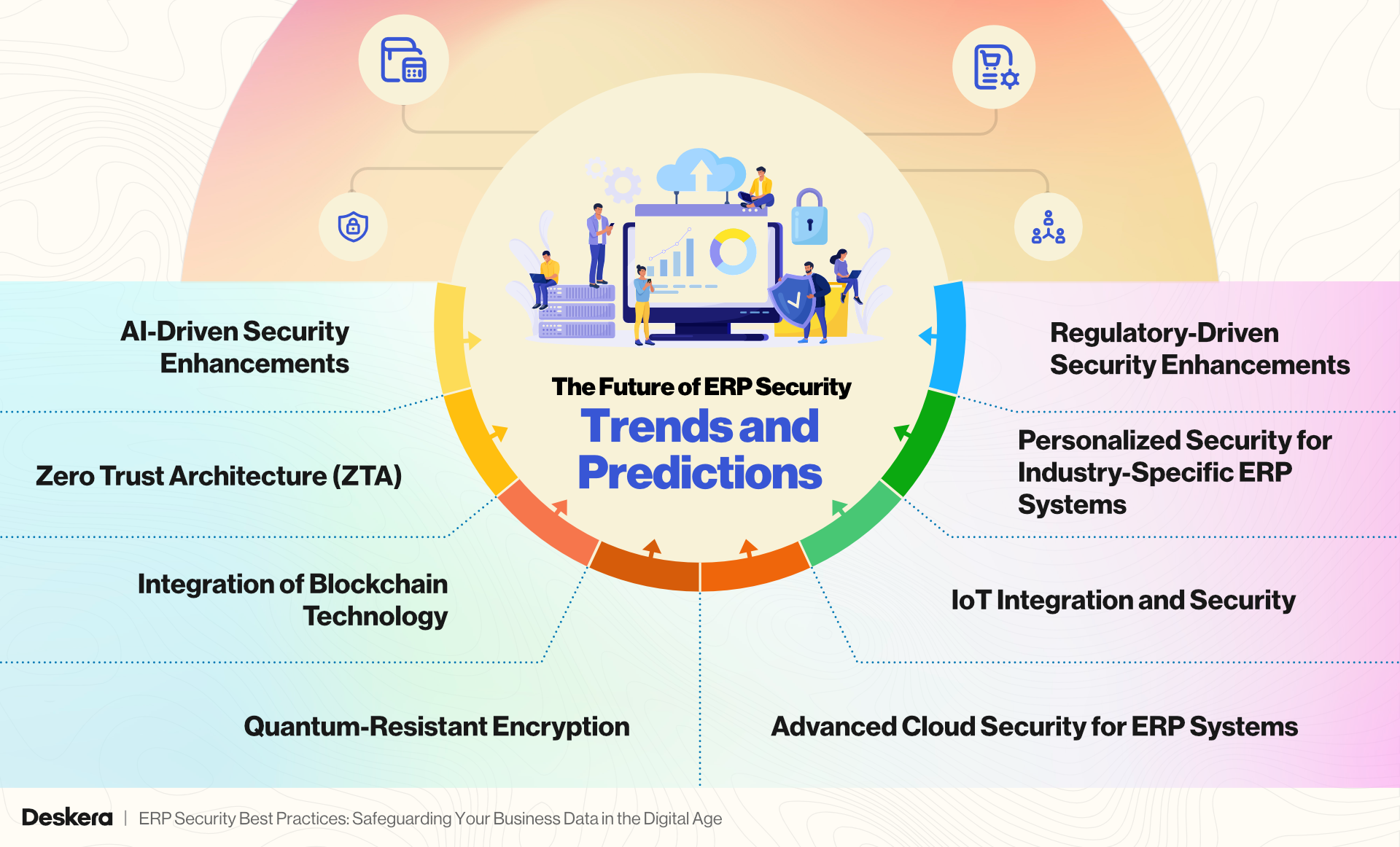
1. AI-Driven Security Enhancements
- Proactive Threat Detection: Advanced AI and machine learning algorithms will analyze vast datasets to predict and identify threats before they manifest.
- Automated Incident Response: AI-driven systems will enable real-time responses to breaches, minimizing downtime and potential damage.
- Behavioral Analytics: Systems will learn user behavior patterns to detect anomalies and flag suspicious activities.
2. Zero Trust Architecture (ZTA)
- End-to-End Verification: The adoption of ZTA will require constant authentication for every user, device, and application accessing ERP systems.
- Micro-Segmentation: Dividing ERP networks into smaller zones will limit the impact of a breach and enhance containment capabilities.
- Policy-Driven Access: Context-aware access policies will ensure that users can only access the data they are explicitly authorized to use.
3. Integration of Blockchain Technology
- Immutable Data Trails: Blockchain will secure ERP transactions with tamper-proof records, ensuring data integrity.
- Enhanced Transparency: Distributed ledger technology will allow organizations to audit data flows and ensure compliance with ease.
- Smart Contracts: Automated contracts within blockchain systems will enforce security policies without manual intervention.
4. Quantum-Resistant Encryption
- Future-Proof Security: As quantum computing becomes a reality, ERP systems will need encryption algorithms capable of withstanding quantum-level processing power.
- Transition Strategies: Vendors will likely start offering hybrid encryption models to bridge the gap between traditional and quantum-resistant methods.
5. Advanced Cloud Security for ERP Systems
- Cloud-Native Security Tools: ERP systems hosted on the cloud will benefit from increasingly sophisticated native security tools, including AI-driven monitoring.
- Compliance at Scale: Cloud providers will enhance their compliance features, ensuring that businesses meet global regulatory standards.
- Dynamic Scalability: Cloud-based ERP solutions will offer adaptable security measures that evolve with organizational needs.
6. IoT Integration and Security
- Securing Connected Devices: As IoT devices become integral to ERP systems, future security measures will focus on authenticating and encrypting device interactions.
- Real-Time Monitoring: IoT security tools will track device behavior, flagging any suspicious activities.
- Firmware Updates: Automated patch management for IoT devices will become a critical feature of ERP security.
7. Personalized Security for Industry-Specific ERP Systems
- Sector-Specific Features: ERP security measures will cater to unique industry requirements, such as compliance for healthcare or financial institutions.
- Tailored Threat Intelligence: Vendors will offer industry-specific threat intelligence to protect against specialized attacks.
- Custom Security Modules: Organizations will have the flexibility to add or modify security features based on their operational needs.
8. Regulatory-Driven Security Enhancements
- Global Compliance Standards: The tightening of data protection laws will push ERP vendors to prioritize security features that meet regulatory demands.
- Data Sovereignty Features: Vendors will offer solutions tailored to regional compliance requirements, such as GDPR or CCPA.
- Auditable Security Features: Future ERP systems will include advanced tools for compliance reporting and real-time auditing.
Deskera ERP and ERP Security: A Robust Approach to Safeguarding Your Business
When it comes to safeguarding business data, Deskera ERP offers a comprehensive security framework that ensures data integrity and compliance while protecting sensitive information.
Below are the key security features of Deskera ERP that help businesses maintain robust security across their operations.
Key Security Features of Deskera ERP
- Data Encryption: Ensures end-to-end encryption for both data at rest and in transit, protecting business-critical information from unauthorized access.
- Multi-Factor Authentication (MFA): Adds an extra layer of security by requiring multiple verification methods for user access, enhancing protection against unauthorized logins.
- Role-Based Access Control (RBAC): Allows businesses to define permissions for each user role, ensuring only authorized personnel have access to sensitive data and functionality.
- Cloud-Based Security: Offers scalable, cloud-native security features that can adapt as businesses grow, ensuring robust protection without compromising flexibility.
- Compliance Tools: Helps businesses maintain regulatory compliance with industry standards like GDPR and ISO/IEC 27001, offering automated reporting and secure data handling.
- Audit Trails and Reporting: Provides detailed logs and audit trails of user activities, making it easier to track and report on security incidents for compliance and troubleshooting.
- Scalable and Proactive Security Measures: Deskera ERP’s security framework is designed to evolve with the growing needs of businesses, offering proactive measures that not only protect current operations but also ensure future resilience against emerging cyber threats. With continuous updates and real-time monitoring, Deskera ensures businesses stay ahead of potential risks.
Key Takeaways
- ERP security is critical for protecting sensitive business data and ensuring the integrity of operations. A robust security strategy helps prevent data breaches, unauthorized access, and compliance violations.
- The rise in cyberattacks targeting ERP systems makes it essential to understand common risks such as phishing, weak passwords, and system vulnerabilities. Proactive security measures are vital to mitigate these risks effectively.
- Strong ERP security not only protects critical business data but also supports regulatory compliance, builds customer trust, and helps organizations avoid costly data breaches that could damage their reputation and bottom line.
- Implementing key best practices, such as multi-factor authentication, regular updates, encryption, and role-based access control, is essential for creating a resilient security framework that safeguards ERP systems against evolving cyber threats.
- Employees are often the weakest link in security. Educating users about common threats, phishing scams, and password hygiene can dramatically reduce the risk of breaches caused by human error.
- Leveraging cutting-edge technologies like AI-driven threat detection, blockchain for data integrity, and quantum-resistant encryption can strengthen ERP security and provide advanced protections against increasingly sophisticated cyber threats.
- When choosing an ERP vendor, it’s essential to assess their security measures, such as data encryption, compliance certifications, and real-time monitoring. A vendor with a strong security track record can help ensure your ERP system is protected against potential threats.
- The future of ERP security will be shaped by innovations like AI-powered security, zero trust models, and quantum-resistant encryption. Staying ahead of these trends will be critical for organizations to maintain robust security in an ever-evolving digital landscape.
Related Articles












